Data governance procedures includes the management of communication assets (e-mail, instant messaging, phone calls), which are considered as business secrets.
While small enterprises should make calculations on using the cloud as the price benefit might worth the negative impact on data management and ownership, a medium/large sized company is suggested to use own solutions with own security and data backup policies.
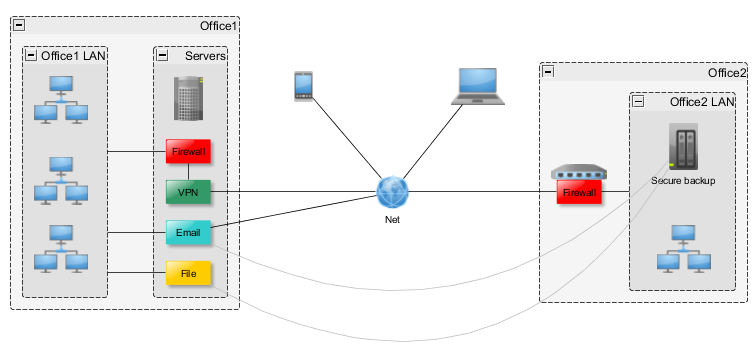
Hereby – in brief – I present an exemplary cost-effective, secure setup for small to medium enterprises own infrastructure based on encrypted communication and messaging storage with data security and backup in mind.
This is a high-level overview: data governance practices, backup policies, disaster recovery, update procedures, security testing, physical security, etc. are to be defined.
Linux based servers: CentOS or Ubuntu
Office 1: ~100-200 users
- Server 1 (Medium)
- VPN connection (OpenVPN)
- VPN tunnel for Office2
- VPN tunnel for mobile workers
- DNS server (Bind)
- DHCP server (DHCPd)
- Firewall (IPTables with Shorewall)
- NET to FW: ALLOW E-MAIL, SSH, VPN ports
- NET to FW and LOC: REJECT
- VPN connection (OpenVPN)
- E-mail
- Postfix server with SSL
- SMTPs
- Postfix server with SSL
- Dovecot mail server
- IMAPs
- Alternative: Zimbra collaboration suite with calendar and file sharing capability
- Instant messaging
- XAMPP
- VoIP
- Elastics bundle
- Harder alternative: Asterisk
- File server
- Owncloud with Dropbox-like services, CalDav and CarDav calendar and contact sync and web interface
- Alternative: Samba for network file system
- Alternative: Zimbra collaboration suite with calendar and file sharing capability
- RSync of all data on VPN to Office2 NAS every night
- Owncloud with Dropbox-like services, CalDav and CarDav calendar and contact sync and web interface
- Nagios with configured alerts (e-mail, SMS)
- LDAP (OpenLDAP)
- SSH (OpenSSH)
- Puppet for configuration management
- Server 2 (Medium)
- Server 1 mirrored, heartbeat with automatic failover
- Puppet for configuration management
- Office 2: ~10-20 users
- Server3 (Micro)
- VPN connection to Office1 with OpenVPN
- All connections through Office1 Firewall
- Firewall (IPTables with OpenWRT)
- VPN connection to Office1 with OpenVPN
- NAS with RAID for data backup
- Server3 (Micro)
- Mobile workers
- Access e-mail only without VPN (CalDav and CarDav can be configured too by firewall HTTP allow and HTTPd .htaccess tweaks)
- Access file share, VoIP and Instant messaging, Office1 internal network with VPN
